Cisco Systems’ latest earnings revealed that its security division grew 18% year-over-year in Q2 2025, outpacing its legacy networking hardware business for the first time in company history. Much of that performance came from its aggressive push into Secure Access Service Edge (SASE), a framework that converges networking and security into a unified cloud service.
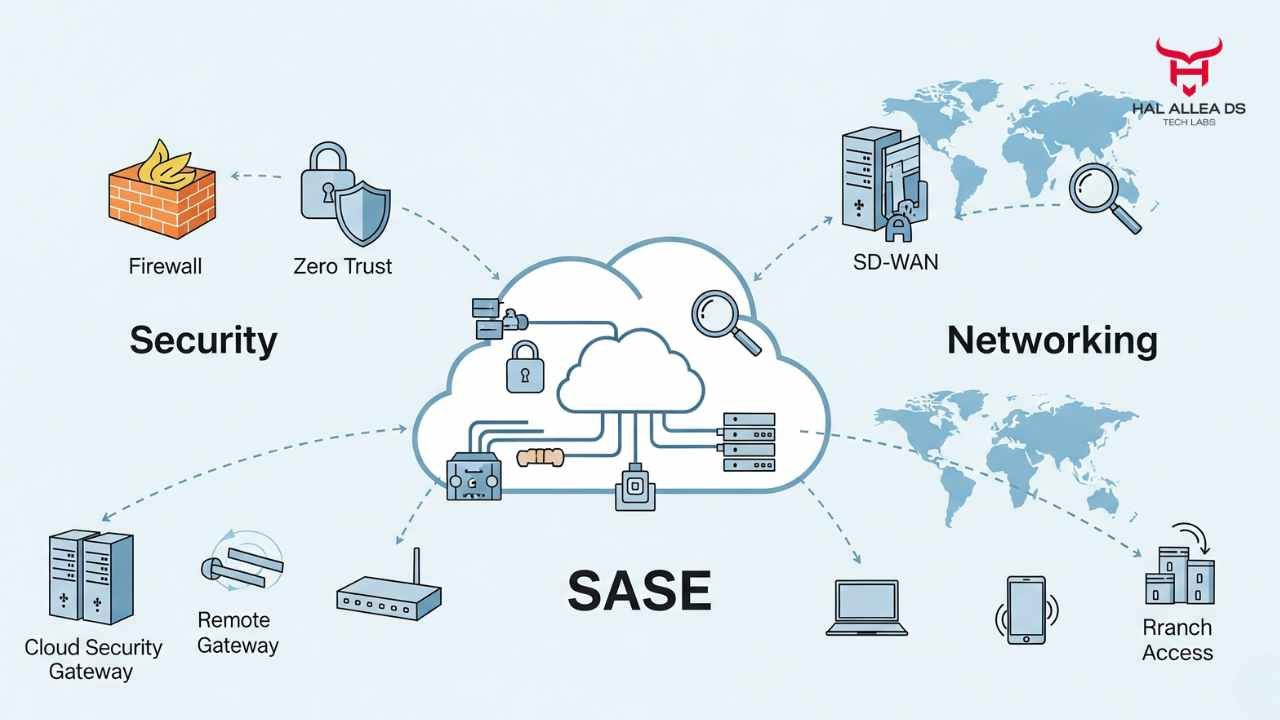
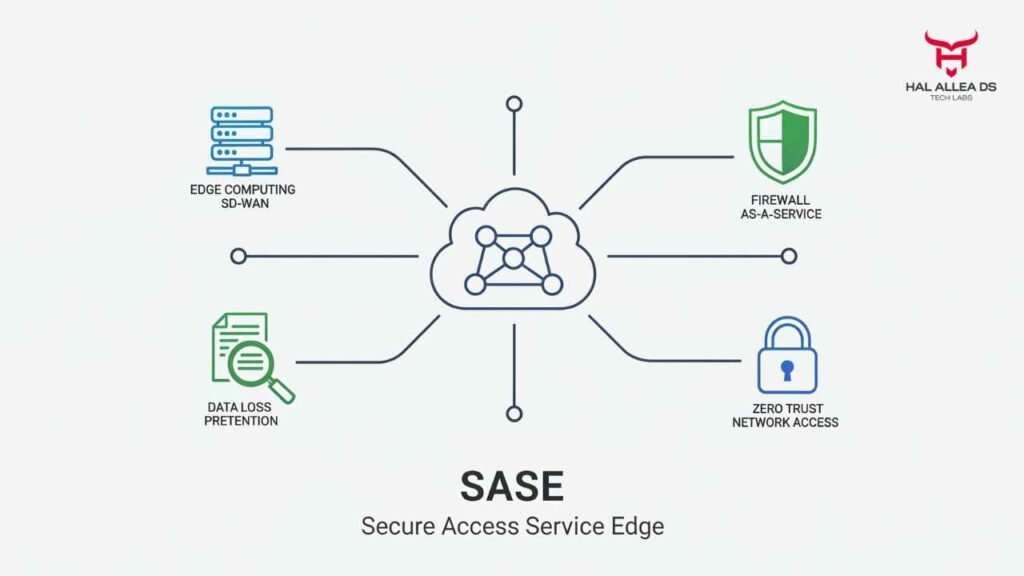
But behind the cheerful numbers sits a thornier story. SASE an architecture that blends networking (SD-WAN) with cloud-delivered security (Zero Trust, CASB, FWaaS) is supposed to simplify the corporate IT stack. Instead, many CIOs complain the transition has been expensive, confusing, and in some cases less reliable than the old patchwork of point solutions.
The winners appear to be vendors like Cisco, Palo Alto Networks, and Zscaler. The losers? IT teams struggling with six-figure cost overruns, employees frustrated by slower connections, and investors who wonder if this is just another over-hyped acronym distracting from deeper systemic problems.
The controversy is clear: while analysts hail SASE as the future of enterprise security, IT leaders complain about vendor lock-in, ballooning costs, and complex rollouts. For investors, the story looks like revitalization at Cisco; for CIOs, it feels more like trading one form of complexity for another. And employees inside security teams, often overworked and understaffed, are stuck reconciling whether this next-gen architecture actually reduces workload—or just repackages it.
The Data
Let’s cut through the marketing speak with what’s measurable.
- Gartner estimates the global SASE market will hit $15 billion in 2025, nearly tripling from just $5.9 billion in 2021. By 2028, projections climb past $25 billion, making it one of the fastest-growing cybersecurity segments.
- According to Bloomberg Intelligence, Cisco now claims about 22% of global SASE deployments, edging ahead of rivals Palo Alto Networks and Zscaler, each at roughly 16–18% market share.
- A 2025 IDC survey of 900 CIOs found that 64% cited “reduced security sprawl” as their top motivation for switching to SASE models. At the same time, 41% admitted overall costs increased in the first year of adoption, often because of overlapping legacy contracts that were difficult to unwind.
- Employee sentiment doesn’t paint a pretty picture either. A Forrester survey from March 2025 found that 40% of end users said SASE platforms slowed down application access compared to legacy VPNs, particularly in regions with weaker ISP peering.
Here’s the thing: the raw growth numbers make SASE look like destiny. But underneath, plenty of CFOs are quietly grumbling that the promised “simplicity” comes tethered to multi-year vendor deals that feel an awful lot like 1990s-style network lock-in.
The People
Voices from inside these transformations tell a more nuanced story.
A senior network architect at a global insurer told Forbes, “Our board approved Cisco SASE on the promise of unified control. A year in, we still run four parallel firewalls because migrating applications isn’t trivial. Meanwhile, Cisco invoices us for everything under the sun. It smells like vendor leverage, not digital transformation.”
Cisco naturally rejects this framing. Jeetu Patel, Cisco’s EVP of Security and Collaboration, said in a recent analyst call: “SASE isn’t about lock-in—it’s about visibility. Customers were drowning in point products. We’re delivering integrated platforms that cut risk at scale.”
But even Cisco insiders acknowledge internal debate. A mid-level sales engineer, who requested anonymity, admitted: “We’ve been told to pitch total SASE adoption even when customers could technically combine best-of-breed vendors. It’s not always about the best tech—it’s about Cisco recapturing wallet share.”
Meanwhile, rivals smell opportunity. Nikesh Arora, CEO of Palo Alto Networks, told Forbes: “There’s no single-vendor future here. True SASE means modularity. If you’re forced to buy a networking stack with security bolted on, that’s not simplification—that’s old-school bundling dressed up as innovation.”
Employees feel the crunch too. A DevSecOps lead at a Fortune 500 energy company described morale challenges: “Our team hoped SASE would reduce incident response complexity. Instead, we got dashboards layered on dashboards. Now developers escalate more, not less.”
The Fallout
The consequences are strategic, financial, and cultural.
For Cisco, the pivot to SASE shields it from the long-declining margins of physical routers and switches. Investors welcome the narrative shift: Morgan Stanley upgraded Cisco to “Overweight” in July, citing “recurring high-margin subscription revenue” as a potential stock catalyst. The shift could extend Cisco’s relevance for another decade.
For enterprises, however, the fallout is mixed. Budget predictability has gone sideways in some cases, with overlapping licensing during transition phases. Gartner analysts note that enterprises often realize net savings only after 2–3 years of steady-state SASE adoption, meaning CFO patience is required. Many firms don’t have that patience when quarterly earnings are on the line.
Customers also face integration fatigue. A European bank reportedly delayed a digital transformation project six months after discovering its SASE rollout broke legacy VPN dependencies for certain regulatory reporting systems. “We thought it’d be seamless,” the bank’s CTO admitted privately. “It’s been anything but.”
At the employee level, turnover is creeping. Security teams attracted by the promise of simplification sometimes find that training curves and migration complexity compound stress. According to LinkedIn workforce analytics, attrition among “SASE engineers” is 14% higher than among traditional network security roles—a sign that reality doesn’t match the recruiting pitch yet.
Here’s where it gets interesting: cloud providers are testing the waters. Sources say Microsoft is piloting SASE ties between Azure and its Entra ID security suite. Amazon lags behind but could choose to partner with Zscaler or Palo Alto rather than build outright. If hyperscalers jump in aggressively, the entire market balance could tip overnight, pressuring Cisco and other traditional players.
Closing Thought
Cisco’s 27% SASE growth would, on the surface, seem like a validation of cloud-delivered secure networking. But scratch beneath that, and the story looks muddier: ballooning customer bills, skeptical engineers, inconsistent performance, and hyperscalers ready to undercut incumbents.
SASE is undeniably on the rise, and Cisco’s early lead makes it look like a blue-chip revival story. But investor optimism doesn’t erase the messiness under the hood: ballooning budgets, migration headaches, and morale issues across enterprise IT teams.
The central question looms large: Will SASE truly deliver on its promise of simplicity and security, or will enterprises discover in two years that they’ve simply traded one set of silos for another—this time wrapped in glossy subscription contracts?