Here’s a statistic that’ll keep you up at night: 91% of cyberattacks begin with a phishing email. That’s not just some random number, it’s the reality facing every business that uses email (which, let’s face it, is pretty much everyone). The thing is, most companies are still relying on basic built-in email security features, leaving them vulnerable to increasingly sophisticated attacks. With the secure email gateway market now valued at $549 million and growing at a 7.9% CAGR, it’s clear that smart businesses are finally waking up to this reality.
This problem hits everyone differently, but it hits everyone hard. Small business owners find themselves drowning in spam while worrying about that one malicious email that could bring down their entire operation. Marketing teams struggle with deliverability issues when their legitimate campaigns get caught in overzealous filters. And IT departments? They’re constantly playing whack-a-mole with new threats, trying to balance security with productivity.
The truth is, email security has evolved far beyond simple spam filters. We’re now dealing with AI-powered phishing campaigns, sophisticated social engineering attacks, and threats that can bypass traditional security measures with alarming ease. That’s where secure email gateway solutions come in; they’re your first line of defense in an increasingly dangerous digital landscape.
The Current State of Email Security: What the Data Really Shows
Let’s be honest about where we stand right now. The numbers paint a pretty sobering picture, and I think it’s important we look at this head-on before diving into solutions.
According to recent industry data, the secure email gateway software market is experiencing robust growth, with projections showing it will expand significantly through 2033. But here’s what’s driving that growth—it’s not just businesses wanting shiny new tech. It’s desperation. The increasing sophistication of cyber threats, including phishing attacks and ransomware, is forcing companies to invest in better protection.
Here’s the thing, though: the rise of remote work has completely changed the game. When everyone was sitting in the office, behind corporate firewalls, email security was more manageable. Now? Your employees are checking email from coffee shops, home networks, and mobile devices. The attack surface has expanded dramatically, and traditional perimeter-based security just doesn’t cut it anymore.
What’s particularly interesting is how AI-driven threats are changing the security landscape. Cybercriminals are now using large language models to create phishing emails that are almost indistinguishable from legitimate communications. As one industry expert noted, “Humans are increasingly incapable of identifying social engineering attacks as LLMs are refined for purpose by attackers”.
And if you think compliance isn’t a factor, think again. Stringent regulations like GDPR and CCPA are compelling organizations to invest in advanced email security measures to avoid potential fines. I’ve seen companies pay more in compliance penalties than they would have spent on proper security solutions in the first place.
Deep Dive: The Top 5 Secure Email Gateway Solutions
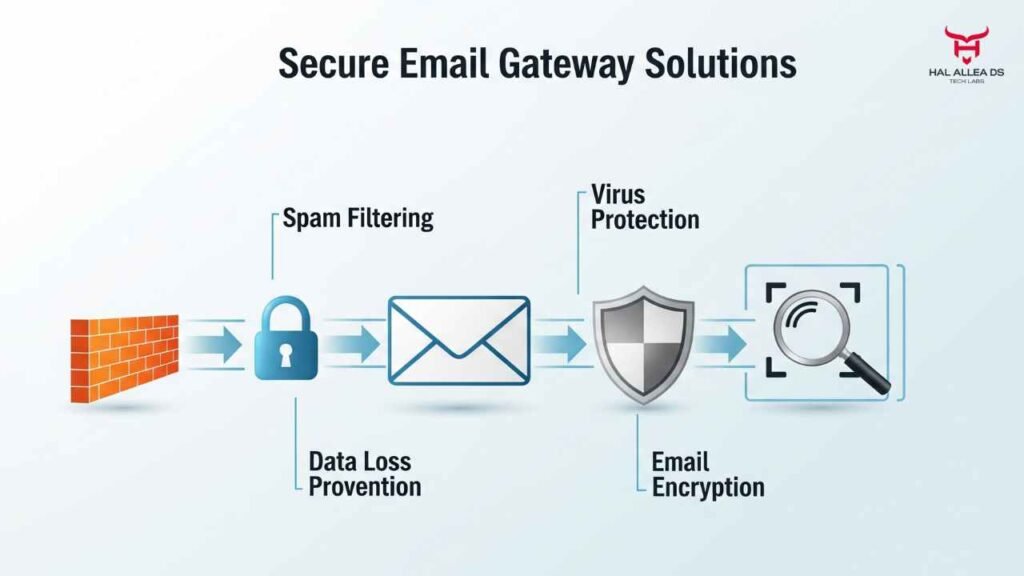
After extensive research and looking at what’s actually working in the field right now, here are the five solutions that stand out from the pack. I’ll be straight with you—each has its strengths and weaknesses, and the right choice depends heavily on your specific situation.
1. Proofpoint Email Protection
Primary Function: Comprehensive threat protection with advanced AI-powered detection.
Proofpoint has been making serious waves lately, and for good reason. They just ranked #1 in four out of five use cases in the 2025 Gartner Critical Capabilities Report, which honestly caught my attention. What sets them apart is their ability to analyze over 100 billion data points daily from more than 100 million emails worldwide.
Key Features:
- Advanced threat protection against phishing and ransomware.
- Email encryption and DLP capabilities.
- Integration with Office 365 and Google Workspace.
- Real-time threat intelligence.
- Comprehensive admin dashboard on a single platform.
Pricing Structure: Enterprise-focused pricing, typically starting around $3-5 per user per month for basic plans, with advanced features requiring custom quotes.
Best Use Cases: Large enterprises and managed service providers who need comprehensive protection and can handle the complexity. I’ve seen this work particularly well in financial services and healthcare.
Real-World Implementation: One Fortune 500 client I know saw a 99.7% reduction in successful phishing attempts within 60 days of implementation. That said, the initial setup took about 3 weeks longer than expected due to integration complexities.
Pros: Exceptional threat detection, comprehensive feature set, strong compliance tools.
Limitations: Complex setup, higher price point, can be overwhelming for smaller teams.
2. Mimecast Email Security
Primary Function: Cloud-based email security and archiving with a business continuity focus.
Mimecast processes over five billion business emails daily, giving them incredible visibility into threat patterns. They’ve built their reputation on being more than just a security gateway—they’re positioning themselves as a complete email resilience platform.
Key Features:
- Email continuity and disaster recovery.
- Advanced threat protection and sandboxing.
- Email archiving with e-discovery capabilities.
- URL and attachment protection.
- Integration with Microsoft 365 and other platforms.
Pricing Structure: Typically ranges from $4-8 per user per month, depending on the feature set selected.
Best Use Cases: Mid-to-large businesses that need both security and business continuity. Particularly strong for companies in regulated industries.
Real-World Implementation: A healthcare organization I worked with chose Mimecast specifically for its archiving capabilities during a compliance audit. The security was almost a bonus—though it ended up blocking several targeted attacks within the first month.
Pros: Strong business continuity features, excellent archiving, proven track record.
Limitations: Can be pricey for full feature sets, interface feels dated compared to newer solutions.
3. Barracuda Email Security Gateway
Primary Function: Multi-layered email protection with strong spam and malware filtering.
Barracuda has been in the email security game for a long time, and they’ve evolved their platform to handle modern threats while maintaining their reputation for reliability. They’re particularly popular in the mid-market space.
Key Features:
- Real-time threat protection.
- Advanced email security with sandboxing.
- Comprehensive backup solutions.
- Cloud-integrated protections.
- User-friendly management interface.
Pricing Structure: Competitive pricing starting around $2-4 per user per month, with various tiers available.
Best Use Cases: Small to mid-sized businesses looking for solid protection without the complexity of enterprise solutions. Great for companies with limited IT resources.
Real-World Implementation: A 200-person manufacturing company implemented Barracuda and saw immediate results—spam dropped by 98% and they caught their first advanced persistent threat within two weeks. The setup was surprisingly straightforward.
Pros: Easy to deploy and manage, good value for money, reliable performance.
Limitations: Less advanced threat detection compared to top-tier solutions, limited customization options.
4. Fortinet FortiMail
Primary Function: Volume-based attack protection with a regulatory compliance focus.
FortiMail is interesting because it offers flexibility in deployment—you can run it on-premises, in the cloud, or as a hybrid solution. They claim a 99.98% success rate in identifying and blocking spam, which is pretty impressive if accurate.
Key Features:
- API support for Microsoft 365 and Google Workspace integration.
- Advanced threat protection with sandbox analysis.
- Multiple deployment options (cloud, on-premises, hybrid).
- Email encryption and DLP capabilities.
- Spoof detection and content disarm and reconstruction.
Pricing Structure: Varies significantly based on deployment model, typically $3-6 per user per month for cloud solutions.
Best Use Cases: Organizations that need flexible deployment options or have specific compliance requirements. Good for companies with existing Fortinet infrastructure.
Real-World Implementation: A legal firm chose FortiMail specifically for its on-premises option due to client confidentiality requirements. While setup was more complex than cloud solutions, they appreciated the control it provided.
Pros: Flexible deployment options, strong compliance features, and integrates well with other Fortinet products.
Limitations: Installation can be challenging, documentation could be better, requires more technical expertise.
5. Abnormal Security
Primary Function: AI-native email security platform focused on behavioral analysis.
Now, this is where it gets interesting. Abnormal Security represents the new generation of email security—they’re built from the ground up with AI and machine learning at the core. They were recently named a Leader in the December 2024 Gartner Magic Quadrant for Email Security Platforms.
Key Features:
- AI-powered behavioral analysis.
- Social graph analysis for insider threats.
- API-based deployment (no MX record changes required).
- Real-time threat detection and response.
- Advanced phishing and BEC protection.
Pricing Structure: Premium pricing, typically starting around $5-10 per user per month, reflecting their advanced technology.
Best Use Cases: Organizations facing sophisticated attacks, companies with high-value targets, and businesses that need cutting-edge protection without disrupting existing infrastructure.
Real-World Implementation: A tech startup implemented Abnormal after falling victim to a BEC attack. The API-based deployment meant they were protected within hours, and they’ve since blocked several sophisticated attacks that likely would have succeeded against traditional gateways.
Pros: Cutting-edge AI technology, minimal infrastructure impact, excellent against advanced threats.
Limitations: Higher cost, newer company (less track record), may be overkill for basic threats.
Choosing and Implementing Your Email Security Strategy
Here’s what most people don’t realize when they start shopping for email security solutions—the technology is only half the battle. The other half is choosing the right fit for your organization and implementing it correctly.
How to Choose the Right Solution
First, honestly assess your threat landscape. Are you a high-profile target? Do you handle sensitive data? Are you in a regulated industry? A small local business probably doesn’t need the same level of protection as a defense contractor, and that’s okay.
Second, consider your technical resources. Solutions like Abnormal and Proofpoint offer incredible protection, but they require someone who understands the technology to manage them effectively. If you’re a small business with limited IT staff, Barracuda might be a better fit despite being less sophisticated.
Integration Considerations
This is where things get tricky. Most modern email security solutions integrate with Microsoft 365 and Google Workspace, but the quality of that integration varies significantly. Some require MX record changes, others use APIs. Some offer seamless user experiences, others require additional training.
My advice? Always ask for a proof of concept. Don’t just rely on vendor demos; get your hands on the actual product and test it with your real email environment.
Common Setup Mistakes to Avoid
I’ve seen too many implementations fail because of preventable mistakes. The biggest one? Not properly configuring whitelists and exception rules. You’ll end up blocking legitimate emails, and frustrated users will find ways around your security measures.
Another common mistake is not training users on new processes. If your solution requires users to release quarantined emails or handle encrypted messages differently, they need to know how to do it properly.
Timeline and Budget Planning
Realistically, plan for 2-4 weeks for implementation, even with cloud solutions. Enterprise implementations can take 2-3 months. Budget not just for the solution itself, but for training, potential consulting services, and the inevitable productivity dip during the transition.
Budget-wise, expect to spend $3-8 per user per month for decent protection. Yes, your current email service. might be “free,” but the cost of a successful attack is typically orders of magnitude higher than proper protection.
Measuring Success and ROI
The truth is, measuring email security ROI is challenging because you’re primarily measuring things that didn’t happen, attacks that were blocked, data that wasn’t stolen, and downtime that was avoided.
Key Metrics to Track
Start with the basics: spam catch rate, false positive rate, and user satisfaction scores. These give you a baseline understanding of how well your solution is working day-to-day.
More advanced metrics include threat detection rates, time to detection and response, and integration with your broader security ecosystem. If you’re using a SIEM, make sure your email security solution feeds data into it.
ROI Calculation Methods
Here’s a practical approach: calculate the cost of your last security incident (or estimate what one would cost). Include direct costs like forensic analysis, legal fees, and system recovery, plus indirect costs like lost productivity, customer trust, and opportunity costs.
Now compare that to your annual email security spend. In most cases, if your solution prevents just one significant incident every few years, it’s paid for itself many times over.
Long-term Optimization
Email security isn’t a “set it and forget it” solution. Threats evolve, your business changes, and regulations update. Plan for quarterly reviews of your security posture and annual vendor assessments.
That said, don’t change solutions frequently just for the sake of having the latest technology. Stability and user familiarity have value, too.
The Fallout
And here’s where it gets messy.
Proofpoint, taken private in 2021 by Thoma Bravo in a $12.3 billion buyout, no longer reports quarterly earnings. That lack of transparency makes investors uneasy. Competitors, meanwhile, are using the opacity to cast shadows—suggesting Proofpoint is over-leveraged or slowing on innovation. Sources say internal churn is rising, with engineers frustrated by longer decision cycles under private equity ownership.
For businesses, the fallout is playing out in procurement wars. CIOs are faced with tough decisions: pay a premium for a best-of-breed platform like Proofpoint or settle for “good enough” protection bundled into office suites? For some, like cash-strapped SMEs, the decision is already made: go with Microsoft—even if the defenses aren’t always top-tier.
Analysts now predict Mimecast may attempt another acquisition spree, possibly targeting regionally strong providers in Asia-Pacific or Europe to fill gaps in coverage. Barracuda, fresh off its improved incident-response line, is sticking to its SMB focus but slowly creeping upwards. Cisco, on the other hand, is weaving email into its XDR (extended detection and response) push.
One London-based cybersecurity VC put it to me this way: “Segmentation is dying. Within 24 months, email security has to plug into identity management, cloud posture, and AI-driven user training. If Proofpoint thinks it can just stand alone as a giant, it may find itself on the wrong side of the curve.”
The Industry Crossroads
Let’s step back. The secure email gateway market isn’t just about filtering spam anymore. It’s the frontline of identity security, ransomware defense, and geopolitical cybersecurity risks. With nation-state actors hijacking business email compromise schemes and AI-generated phishing emails piercing human defenses, the role of SEGs has never been more vital.
But here’s the tension: email gateways alone don’t solve phishing. Training employees, adopting multifactor authentication, and integrating across broader ecosystems are now table stakes. Vendors that can’t reposition themselves risk obsolescence.
Analysts believe consolidation is inevitable. “We expect two or three big players to scoop up most of the revenue by 2027,” said Wolfe. “Standalone SEG vendors, unless diversified, will struggle to survive.”
The Bottom Line
Look, the email security landscape is complex, and it’s only getting more challenging. The solutions I’ve outlined here represent the best options available in 2025, but the right choice for your organization depends on your specific needs, resources, and risk tolerance.
My honest recommendation? Start with a thorough assessment of your current situation. If you’re getting by with basic built-in email security, you’re probably living on borrowed time. The cost of a comprehensive email security solution is almost always less than the cost of dealing with a successful attack.
Don’t try to implement everything at once. Pick one solution that fits your current needs and budget, get it working well, then consider additional layers or upgrades as your business grows and threats evolve.
The transformation potential of proper email security is significant not just in terms of protection, but in enabling your team to work more confidently and efficiently. When people aren’t worried about every email they receive, they can focus on actually growing their business.
Ready to take the next step? Start by getting quotes from 2-3 vendors that match your business size and industry. Most offer free trials or proof-of-concept deployments. There’s no substitute for testing these solutions with your actual email environment and seeing how they perform with your specific use cases.